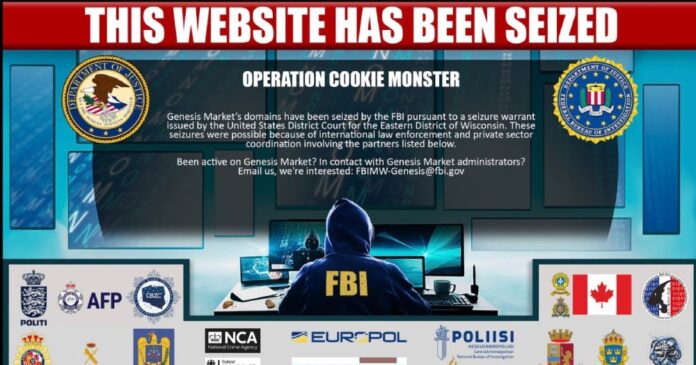
U.S. and international law enforcement agencies have seized Genesis Market as part of the “Operation Cookie Monster” – as the FBI calls it.
The hacker marketplace that is used to acquire compromised credentials and digital browser fingerprints now shows a notice stating that U.S. law enforcement officials have executed a seizure warrant.
“Genesis Market’s domains have been seized by the FBI pursuant to a seizure warrant issued by the United States District Court for the Eastern District of Wisconsin,” the website reads.
Aside from the FBI, the takedown involved law enforcement agencies from the United Kingdom, Europe, Australia, Canada, Germany, Poland and Sweden.
The operation also saw about 120 people arrested and 200 searches carried out globally. The U.K.’s National Crime Agency arrested 19 suspected site users, including two men aged 34 and 36, who are being held on suspicion of fraud and computer misuse. The FBI also made some arrests in the U.S., though at the moment, we don’t have exact numbers.
“This is the biggest operation of its kind. We’re not just going after administrators or taking sites down; we’re going after users on a global scale,” a senior FBI official told TechCrunch. They added that they have also identified approximately 59,000 users of the marketplace.
As part of the process, the FBI provided data breach notification website Have I Been Pwned with “millions” of email addresses and passwords from the Genesis Market — which internet users can check to see if they were compromised.
Genesis Market has been in business since 2017 as an invitation-only online marketplace that sells stolen credentials, cookies, and digital browser fingerprints gathered from compromised systems. These fingerprints included IP addresses, session cookies, plugins, and operating system details — enabling attackers to impersonate victims’ browsers to access their online banking and subscription services without needing the victim’s password or two-factor authentication.
According to Genesis, these browser fingerprints would be kept up to date for as long as it retained access to a compromised device.
“In other words, Genesis customers aren’t making a one-time buy of stolen information of unknown vintage; they’re paying for a de facto subscription to the victim’s information, even if that information changes,” Yusuf Arslan Polat, a senior threat researcher at Sophos, said in an analysis of Genesis Market last year.
Back to the FBI, which said that Genesis Market offered access to data stolen from more than 1.5 million compromised computers worldwide — containing over 80 million account access credentials. They also noted that Genesis had made at least $8.7 million from the sale of stolen credentials, adding that complete total losses likely exceed tens of millions of dollars.
Kudos to the FBI and other agencies involved in this operation; now, if you could also stop following us — regular users — that would be a blast. Is online privacy too much to ask?
